identity privacy
Introduction: The Importance of Identity Privacy in the Digital Age
In the digital era, our personal data has become one of the most valuable commodities. From social media platforms to online banking, we are constantly sharing sensitive information that, if not adequately protected, can be exposed to malicious actors. Identity privacy is the cornerstone of cybersecurity, playing a critical role in protecting individuals from identity theft, fraud, and data breaches.
Identity privacy refers to the ability to control who has access to your personal information and ensuring that this information is protected from unauthorized access. As digital threats continue to evolve, individuals and businesses alike are turning to specialized privacy tools to secure their personal data.
This article will explore the essence of identity privacy, its relevance in today’s digital world, and the technological solutions available to protect personal information. We will also examine the market trends, challenges, and opportunities within the identity privacy space.
1. Understanding Identity Privacy: A Deep Dive into Personal Data Protection
At its core, identity privacy is about protecting the information that defines an individual’s digital persona. This can include everything from your name, address, and date of birth, to your financial records, medical history, and even social media interactions. In an age where data is often seen as the "new oil," personal data has become a highly sought-after resource for hackers and companies alike.
Key Aspects of Identity Privacy:
- Data Encryption: A key feature of identity privacy tools is the ability to encrypt data, ensuring that even if it is intercepted, it cannot be read or used.
- Anonymity: Some privacy tools offer the ability to remain anonymous online, preventing third parties from tracking your activity or accessing your personal details.
- Two-Factor Authentication (2FA): A critical feature in many identity privacy products, 2FA adds an extra layer of security to ensure that even if a password is compromised, unauthorized access is still prevented.
- Secure Data Storage: This feature ensures that personal data is stored securely, often through cloud-based encryption, preventing unauthorized access or leaks.
As individuals share more personal information online, the need for robust protection mechanisms grows. Identity privacy products are designed to address this demand, providing users with the tools to protect their digital identities from threats like identity theft and unauthorized data collection.
2. Product Features: The Technical Backbone of Identity Privacy Solutions
Identity privacy solutions are equipped with a range of features designed to provide comprehensive protection for individuals and businesses. Below, we will explore some of the most critical product features in detail, offering insights into how these technologies work and why they are essential for maintaining privacy in the digital world.
a. Data Encryption: Protecting Personal Information at the Core
Data encryption is one of the primary methods used by identity privacy tools to safeguard information. By converting personal data into unreadable code, encryption ensures that even if data is intercepted during transmission or stored in a compromised location, it cannot be accessed without the appropriate decryption key.
- Symmetric Encryption: This method uses a single key for both encryption and decryption, making it efficient for securing large amounts of data.
- Asymmetric Encryption: This method employs two keys—a public key for encryption and a private key for decryption—providing additional layers of security.
Encryption is the foundation of many identity privacy tools, ensuring that personal data remains secure even in the event of a data breach.
b. VPNs: Anonymizing Online Activity
Virtual Private Networks (VPNs) are another essential feature of many identity privacy tools. VPNs mask a user’s IP address, rerouting their internet traffic through a secure server and making it difficult for third parties to track their online activity. This not only protects personal information but also helps users maintain anonymity online.
- Location Masking: By hiding a user’s physical location, VPNs prevent websites and services from tracking their whereabouts.
- Data Encryption: VPNs often combine encryption with location masking, ensuring that any data transmitted during a browsing session is secure.
c. Password Managers: Strengthening Access Control
Weak passwords are one of the most common ways hackers gain access to personal accounts. Password managers help mitigate this risk by generating and securely storing complex, unique passwords for each account. With features like automatic password generation, multi-device synchronization, and 2FA integration, password managers play a vital role in identity privacy.
- Password Encryption: Password managers encrypt stored passwords, ensuring that even if the manager itself is compromised, the passwords remain secure.
- One-Click Login: Many password managers offer features like auto-fill, which simplifies the login process while maintaining security.
3. Market Analysis: Trends and Opportunities in the Identity Privacy Industry
The identity privacy market has experienced exponential growth in recent years, driven by an increasing number of cyberattacks, data breaches, and a growing awareness among consumers about the importance of personal data protection.
a. Rising Cybersecurity Threats
The growing sophistication of cybercriminals has created an urgent need for stronger identity privacy solutions. From phishing scams to ransomware attacks, the risks of personal data exposure are higher than ever before. As a result, demand for identity privacy tools—especially those offering encryption, anonymization, and breach protection—has skyrocketed.
b. Regulatory Frameworks: Driving Adoption
Government regulations like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the U.S. have also played a significant role in increasing the adoption of identity privacy solutions. These regulations impose strict requirements on businesses regarding the collection, storage, and use of personal data, compelling companies to invest in privacy tools that protect user information.
c. Technological Advancements: New Frontiers in Privacy Protection
As technology evolves, so too do the tools and techniques used to protect personal data. Innovations such as blockchain-based identity management, artificial intelligence (AI)-driven threat detection, and biometric authentication are pushing the boundaries of what is possible in identity privacy protection.
Blockchain for Identity Privacy: Blockchain technology offers decentralized identity management solutions, enabling individuals to control their personal information without relying on third-party intermediaries. This provides a more secure and transparent method for managing personal data.
AI-Powered Privacy Tools: AI algorithms can monitor user behavior, detect anomalies, and predict potential threats, making privacy tools more proactive in safeguarding personal information.
d. Market Growth Projections
According to market reports, the global identity and access management (IAM) market—which includes identity privacy solutions—is projected to reach USD 24.1 billion by 2025, growing at a compound annual growth rate (CAGR) of 13.1%. This growth is fueled by increasing investments in cybersecurity, rising regulatory pressures, and the expanding adoption of cloud-based identity management solutions.
4. Target Audience: Who Needs Identity Privacy the Most?
Identity privacy solutions cater to a broad range of users, from individual consumers looking to protect their personal data to large enterprises seeking to secure customer information and internal systems.
a. Individual Users
For everyday internet users, protecting personal data is paramount. Whether it’s shielding financial information from hackers or preventing social media accounts from being compromised, identity privacy tools offer a critical layer of security.
Online Shoppers: With e-commerce on the rise, individuals are increasingly sharing sensitive payment details online. Identity privacy solutions can protect financial data during transactions, ensuring that credit card information and other personal details are not exposed.
Social Media Users: As social media platforms collect vast amounts of personal data, users are turning to privacy tools to limit what these companies can access and to safeguard their accounts from hackers.
b. Businesses and Enterprises
In the corporate world, protecting customer data is not only an ethical obligation but also a legal requirement. Enterprises are investing heavily in identity privacy solutions to prevent data breaches and comply with regulations like GDPR and CCPA.
Financial Institutions: Banks and other financial services are prime targets for cybercriminals, making identity privacy a top priority. Solutions like multi-factor authentication and data encryption help protect sensitive financial information from breaches.
Healthcare Providers: Healthcare organizations handle vast amounts of personal and sensitive data, including medical records. Identity privacy solutions help these organizations comply with regulations like HIPAA while safeguarding patient information.
c. Remote Workers
With the rise of remote work, employees are increasingly accessing company systems from home or public networks, raising the risk of cyberattacks. Identity privacy solutions, such as VPNs and secure authentication methods, are essential for remote workers to maintain secure access to corporate networks.
5. Challenges and Solutions: Addressing the Pain Points in Identity Privacy
While identity privacy tools offer critical protection, they are not without challenges. From user convenience to cost concerns, understanding and overcoming these hurdles is essential for widespread adoption.
a. Balancing Security with Convenience
One of the main challenges in identity privacy is striking the right balance between security and user convenience. For example, while multi-factor authentication (MFA) provides robust protection, some users find it inconvenient to use on a regular basis.
Solution:
Many privacy tools are focusing on user experience (UX), developing seamless authentication methods that don’t compromise security. For instance, biometric authentication (e.g., fingerprint or facial recognition) offers a convenient alternative to traditional MFA methods.
b. Cost Concerns for Small Businesses and Individuals
For small businesses and individual users, the cost of implementing comprehensive identity privacy solutions can be prohibitive.
Solution:
Freemium models and scalable pricing structures are helping to make privacy tools more accessible. Many identity privacy tools offer free versions with basic features, allowing users to access essential protection at no cost. As their needs grow, they can upgrade to premium versions for more advanced functionality.
c. Ensuring Compliance with Global Privacy Laws
As privacy regulations differ from region to region, businesses operating on a global scale may face challenges in ensuring compliance with all applicable laws.
Solution:
Many identity privacy tools offer built-in compliance features, helping businesses navigate the complex landscape of global data privacy laws. These tools can automatically adjust privacy settings to meet the requirements of different jurisdictions, ensuring that businesses remain compliant without the need for manual adjustments.
Conclusion: The Future of Identity Privacy
As the digital landscape continues to evolve, the importance of identity privacy will only increase. With rising cyber threats and growing awareness among consumers about the value of their personal data, the demand for robust identity privacy solutions is set to surge.
The future of identity privacy lies in advanced technologies such as blockchain, artificial intelligence, and biometric authentication, which promise to offer even greater protection and convenience. As businesses and individuals become more conscious of the need for data protection, identity privacy solutions will continue to play a crucial role in safeguarding personal information and ensuring security in an increasingly interconnected world.
Investing in identity privacy is not just a choice—it is a necessity for anyone who wants to protect their digital footprint and stay secure in today’s ever-evolving digital ecosystem.
 ID market trends
ID market trends
 identity privacy
identity privacy
 advanced ID technology
advanced ID technology
 fake ID technology
fake ID technology
 ID verification loopholes
ID verification loopholes
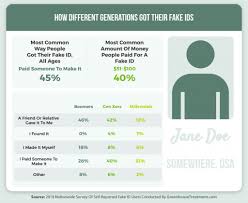 fake identification industry
fake identification industry
 fake Florida driver’s license
fake Florida driver’s license
 security measures
security measures
